
22 Aug What is PowerG?
What is PowerG?
PowerG uses revolutionary 2-way wireless communication technology that decreases operational costs while providing ultimate reliability for end users. PowerG devices reliably communicate 4 times further than legacy wireless security, reducing the cost of installing additional repeaters to service commercial premises. The typical range is around 6,500 feet in open-air environments.
Additionally, the wireless protocol includes Multi-channel, Frequency Hopping Spread Spectrum technology, Adaptive Transmission Power for up to eight years of battery life, and 128-bit AES encryption for exceptional protection against digital attacks.
Why use Power G?
Today, wireless communication is part of daily life. Users have gained full confidence in wireless performance and rely on numerous wireless devices used in their home and work lives. Wireless communication is everywhere we turn, and it affects everything in multiple ways.
With intrusion alarm systems, this trend is no different. The shift from hard-wired to wireless alarm systems has been rapid. Now, wireless technology is increasingly accepted for security applications in residential and business premises. Security installers are standing behind wireless alarm systems. This allows for consumer adoption and insurance companies’ acceptance of technologies that they didn’t once consider trustworthy enough for security.
An additional driver for wireless security is the growth of the connected home. As more homes and businesses adopt networks allowed varying degrees of automation, the demand for wireless security devices is increasing. A study released by Radiant Insights in mid-2015* projected that worldwide sales of security devices for the connected home would grow from about $1.2 billion in 2014 to over $7.5 billion by 2021.
PowerG Key Features:
- Frequency Hopping Spread Spectrum – Signal can’t be jammed because it’s always moving.
- Full Two-way Synchronized TDMA Communication – Users can share the same frequency channel without causing interference.
- Secured Wireless Communication with AES Encryption – An advanced encryption algorithm for correct message identification (prevents hackers).
- Unmatched Benefits with a Breakthrough Technology – See features below.
*Note: descriptions below use a lot of technical phrases. For a simple explanation, watch the video listed above.
Frequency Hopping Spread Spectrum
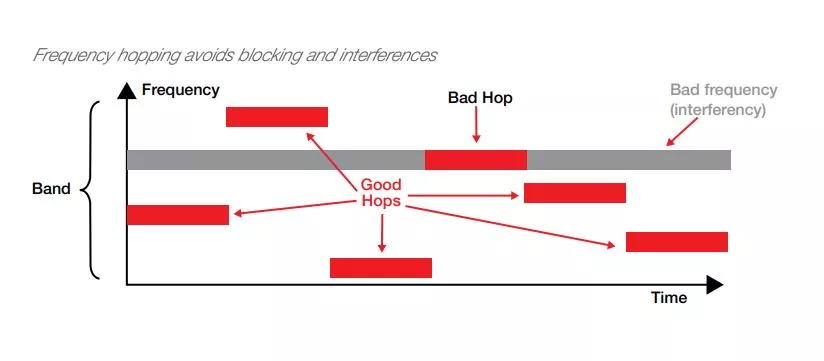
Frequency Hopping Spread Spectrum (FHSS) derives from military radio technology, making it secure and reliable under adverse battle conditions. FHSS changes the frequency of a transmission at intervals faster than an intruder can re-tune a jamming device. With FHSS, it divides the bandwidth into multiple frequency channels. Once it establishes a wireless connection and gains time-synchronization, the receiver and transmitter agree on one of practically infinite frequency hopping sequences. These sequences are both encrypted and time-dependent. Based on the current time and a mathematical calculation, both the receiver and transmitter hop to the next frequency channel in the sequence at the same time. Unless the system time, the system encryption key and the proper calculation are all known, you can’t track the communication. As a result, unauthorized interception of, or eavesdropping on, a communication is virtually impossible.
How does Power G use it?
The PowerG network uses Frequency Hopping Spread Spectrum technology. The network continuously hops between multiple frequencies spread over the entire assigned frequency band: 8 hopping frequencies in the 433-434MHz bands, 4 hopping frequencies in the 868-869MHz bands, and 50 hopping frequencies in the 912-918MHz bands.
The network does not remain in a single frequency but switches frequencies 64 times a second, using an encrypted unique pseudo-random sequence known only to devices enrolled to the PowerG panel. The pseudo-random sequence differs from one PowerG panel to another.
By using FHSS technology, the PowerG network successfully overcomes intentional and un-intentional interferences and jamming. Multiple PowerG-based alarm systems can operate in the same vicinity without interfering with each other. Robustness and reliability of the wireless network increases dramatically. An analogy to FHSS is as follows: Imagine a car driven in a multi-lane highway. As a strategy, the driver continuously and rapidly changes lanes. If something blocks one of the lanes (like road work or a road accident), the car will avoid the disturbance because it is changing lanes continuously. The following figure illustrates the FHSS concept.
Full Two-way Synchronized TDMA Communication
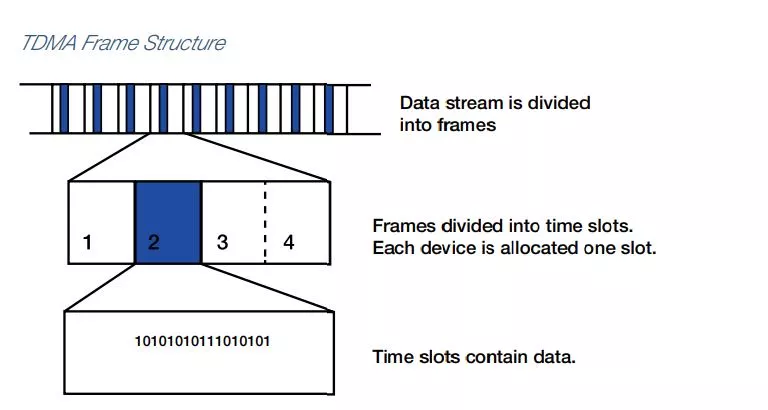
TDMA (Time Division Multiple Access) is a digital transmission technology that allows a number of users to access a single radio-frequency (RF) channel without interference by allocating unique time slots to each user within each channel.
The users transmit in rapid succession, one after the other, each using their own time slot. This allows multiple users to share the same transmission medium (e.g. radio frequency channel) while using only part of its channel capacity. Multiple users, therefore, can share the same frequency channel without causing interference because it divides the signal into multiple time slots. Each time slot acts as a separate communication path. TDMA relies upon the fact that the signal has been digitized – divided into milliseconds-long packets. It allocates a single frequency channel for a short time and then moves to another channel. TDMA is used in digital cellular systems such as GSM.
Many panels have one way communication, however 2-way encryption is major step up. For example with 2-way encryption, your sensor will communicate more frequently to the panel and vice versa, whereas a regular one way communication line only goes through once and is more prone to communication/interference errors.
Similar to the GSM cellular network, each device in the PowerG network is allocated unique time slots for full two-way data transmission with the panel, streamlining communication and increasing channel efficiency. This eliminates RF collisions and assures that no alarm or supervision message is lost.
TDMA and Power G
TDMA technology allows a low-latency, low-power downlink channel, which is vital to minimizing power usage while maintaining required performance. PowerG-powered devices are mostly dormant; they wake up frequently and periodically, switching on their receiver for a fraction of a millisecond, during which downlink messages can be sent. In this way, they are instantly responsive to a transmitted message, with minimum awake time.
Sleepy PowerG devices are time-synchronized to within +/- 30 µSEC, with an energy consumption footprint of less than 2 µA. This response time works to provide the services needed for the full range of home/business security and safety applications, including heavy-duty applications like battery operated sirens that you need to activate within a fraction of a second. In this way, TDMA technology provides the devices with extended battery life since the device is only transmitting a portion of the time. They also avoid repeated transmissions, resulting in an energy-saving network.
Here’s an analogy to the PowerG synchronized TDMA communication: imagine a meeting attended by several people. When communication doesn’t synchronize, participants speak simultaneously, creating interferences and communication blocks. On the other hand, if a moderator manages a meeting by controlling who speaks by a complex set of rules and a rigid clock, each participant restricts his or her speaking to a specific time-slot, and everyone else remains silent. This makes the meeting more effective.
Secured Wireless Communication with AES Encryption
AES (Advanced Encryption Standard) is a symmetric (private key) encryption standard, originally published as Rijndael in 1998 and adopted by the U.S. government in 2000. In 2001, NIST (National Institute of Standards and Technology) chose AES as the Federal Information Processing Standard (FIPS). In 2003, the National Security Agency (NSA) stated that AES was secure enough to protect its information at the secret and top-secret levels.
How does it work?
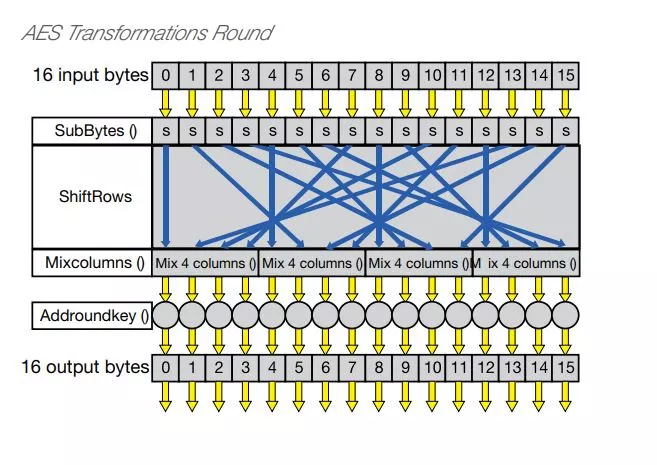
AES consist of three block ciphers. Each cipher has a 128-bit block size with three different key sizes of 128, 192, and 256 bits. The algorithm is based on permutations and substitutions. Permutations are rearrangements of data, and substitutions replace one unit of data with another. AES performs permutations and substitutions using several different techniques.
The AES cipher repetitively performs a number of transformation rounds, thus converting the input plain data into an output of cipher data. There are several processing steps for each round, with one round that relies exclusively on the encryption key. Then, a set of reverse rounds convert the cipher data back into plain data.
The AES encryption uses a single key which is a shared secret between the sender and receiver to encrypt and decrypt data. An analogy is a locked mailbox without a mail slot. Anybody who wants to leave or read a message needs to have a key to the mailbox.
AES encryption and PowerG
The PowerG network employs the proven AES-128 (128 bit key) advanced encryption algorithm for correct message identification and for protecting the alarm system from code grabbing and from message substitution by hackers and other attackers. AES-128 uses 10 rounds with each round performing several transformations.
AES is a well-proven encryption algorithm that guarantees strong authentication and encryption security for the PowerG wireless network.
Unmatched Benefits with a Breakthrough Technology
The combination of technologies—Frequency Hopping Spread Spectrum (FHSS), synchronized TDMA communication, and AES—gives PowerG immense strength to deliver a new, advanced alarm system that provides unmatched advantages for professional installers, central monitoring stations and end-users alike. In fact, PowerG provides the convenience of a wireless network with reliability closer than ever to that of a hard-wired one. Here are some additional features of PowerG.
Energy-saving network
Each device continuously measures communication quality and automatically sets its transmission power to the minimum required for reliable communication with the panel. Full, two-way synchronized communication ensures minimum, short transmissions. These significantly extend the battery life of PowerG devices to exceed 8 years. Additionally, it reduces on-site maintenance visits since the system can support numerous functions remotely.
Unmatched robustness and reliability
Signals continuously hop between channels in a random sequence, avoiding interferences and jamming. TDMA communication ensures to eliminate RF collisions.
Surpasses most industry security standards
The PowerG network employs the proven AES-128 encryption algorithm. It protects the system from code grabbing and message substitution by hackers and other attackers.
Huge transmission range
PowerG employs advanced radio and diversity antenna technologies that, when combined with frequency hopping and synchronized TDMA communication, result in an extremely large range—far greater than the industry standard. This enables repeater-free installations even on very large premises. Tests reveal a line of sight communication range greater than 2km (6,000ft)*. By adding a PowerG repeater the range can be doubled.
Support for advanced applications
PowerG handles a substantially high bandwidth, enabling the network to transmit large amounts of data in a short time. This provides the infrastructure for solutions such as installations with numerous devices, audio and video applications. Additionally, as a proprietary technology, PowerG supports mobile apps developed specifically to provide real-time visibility and control of PowerG home and business security alarm systems.
Advanced, time and money-saving toolset
The PowerG full two-way uplink and downlink data communication provides installers with powerful tools, unmatched in our industry, that can save time and money on a daily basis. The toolsets include: quick and easy installation with built-in link quality indicators on the devices; on-site and remote configurations of devices and peripherals; cost-saving advanced on-site and remote diagnostics—the system continuously diagnoses the RF environment and interferences at the site and provides (locally and remotely) meaningful information to help understand and resolve problems; remote real time testing and walk testing of the system.
* In actual installations, construction signal attenuation reduces the range.
Summary
PowerG Technology is one of the leading technologies targeted to this growing market segment. It’s specifically for the monitoring and control of battery-operated devices for security and safety applications for homes and businesses. This technology works as the world’s best live security and live safety technology. It can cover any building without running expensive wires or conduit. So it fully addresses the key requirements for wireless security systems: reliability, performance, privacy, vulnerability, usability, and maintenance.
While Frequency Hopping Spread Spectrum, TDMA communication, and AES are not new technologies, it’s the implementation of all three within PowerG that makes this system so innovative and revolutionary. This combination in these intrusion alarm systems fully answers the urgent needs of our industry. By creating an energy-saving, highly robust and reliable network and providing long transmission range, an advanced, time-saving toolset, and support for advanced applications and mobile control, our PowerG-based intrusion alarm systems fully answer the urgent needs of our industry.


No Comments